Weaponized Coronavirus Phishing & How to Protect Yourself
It was only a matter of time before bad actors began preying on people’s fear of the coronavirus pandemic—and that time is now. Phishing campaigns with mock-up coronavirus (COVID-19) heat maps and links to malicious sites are cropping up everywhere, and companies need to know how to identify and deal with them.
How to Spot a Coronavirus Phishing Email
Phishing emails appear to be from a trusted source, tricking you into providing sensitive information, downloading malware, or clicking a link to a website that can do either.
Attackers craft phishing emails that mimic those from the World Health Organization (WHO) and the Centers for Disease Control and Prevention (CDC)—some even claim to be from the WHO or the CDC.
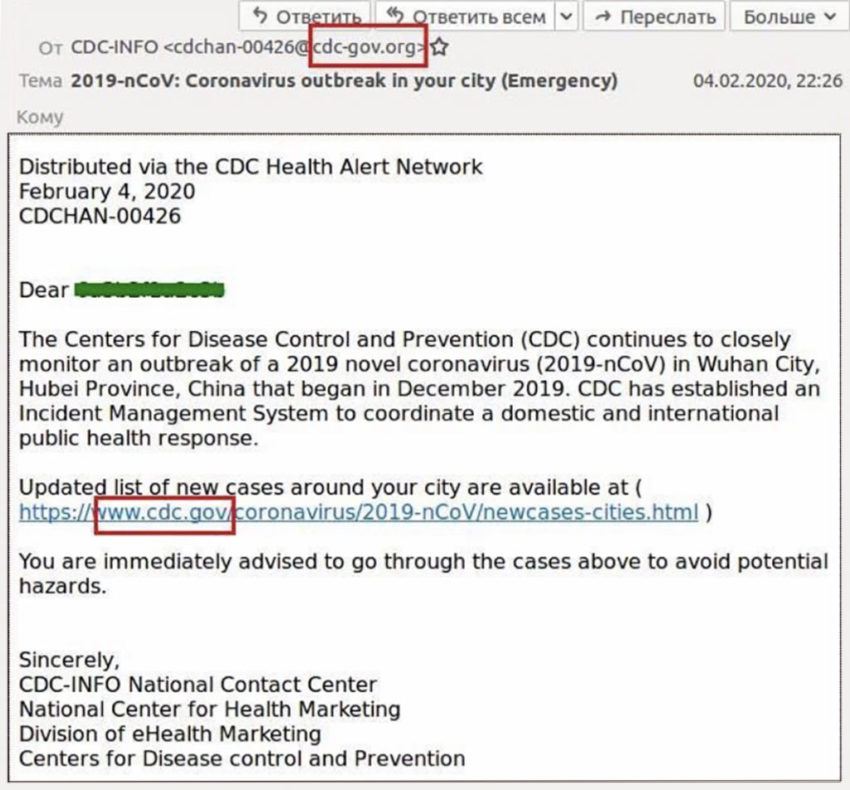
Readers are lured in with a subject line or copy claiming to have news about infections or the virus itself. These phishing emails hit pain points by offering a link to a coronavirus map of the recipient’s neighborhood or an update on how many people have been infected.
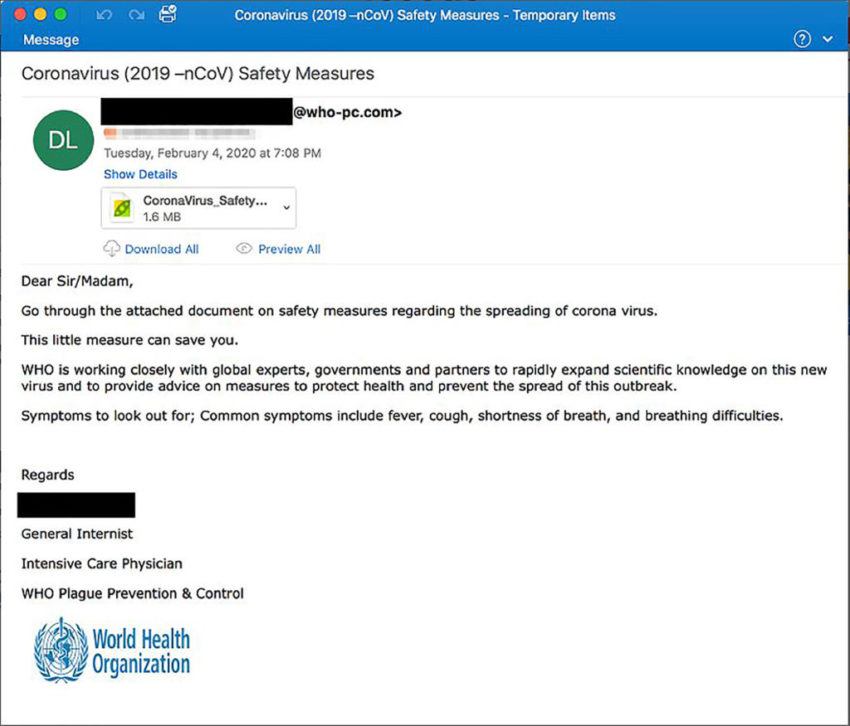
How Coronavirus Phishing Emails Work
Many times, bad actors are targeting users interested in maps representing the infection rate of COVID-19. These attackers show a map loaded from a legitimate online source (e.g., the Johns Hopkins Coronavirus Resource Center), then trick users into downloading and running a malicious application.
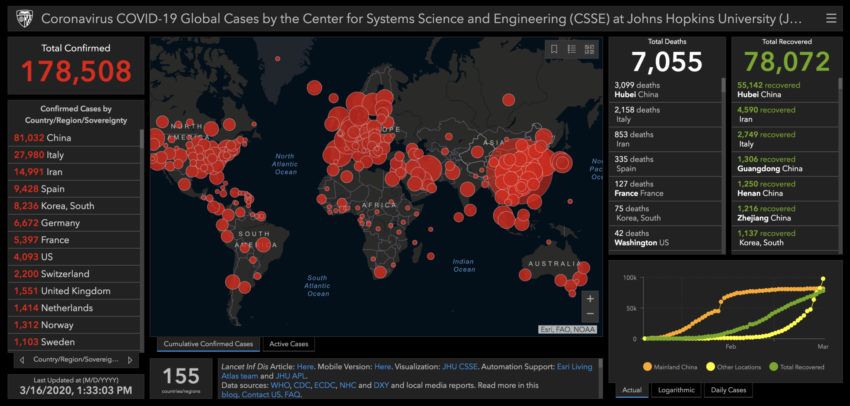
Phishing emails almost always require users to click a link to see information or a map. When a user visits this fake site, it prompts them to download and run an executable file that mimics the Johns Hopkins heat map website and allows malware to run in the background. This malware searches the localhost in an attempt to steal financial and other sensitive data and then sell it on the dark web. This malware is also used to download other malicious payloads and infect other hosts on the network.
Reason Labs’ analysis says the demand for information “creates a vulnerability that malicious actors have quickly taken advantage of by spreading malware disguised as a ‘coronavirus map.’” Reason Labs’ Shai Alfasi “found and analyzed this malware that had weaponized coronavirus map applications in order to steal credentials such as user names, passwords, credit card numbers and other sensitive information that is stored in the users’ browser.”
A few days ago, the WHO put out a warning about phishing attempts via emails that appeared to be from WHO representatives. The agency is receiving reports of coronavirus-related phishing attempts almost daily, according to the Wall Street Journal. Meanwhile, cybersecurity firm Proofpoint has also found a rash of WHO-branded phishing attempts, as well as coronavirus-themed phishing emails from other health-related organizations. Alarmingly, some of these phishing attempts appear to come from internal company emails.
Over 4,000 coronavirus related domains (containing words like “corona” or “covid”) have been registered since the beginning of 2020. Of those, 3% were considered malicious, and another 5% were suspicious. 3% may not seem like much, but this means that a coronavirus-related domain is 50% more likely to be malicious than any other domain registered during the same period. And many of those malicious sites will be used in phishing campaigns.
Avoid Coronavirus Phishing Scams
Here are some tips to help you recognize phishing when you see it.
- Don’t click on links from sources you don’t know. Those links could download viruses onto your computer or device.
- Watch for emails claiming to be from the CDC or experts with information about COVID-19. For the most up-to-date information about the coronavirus, visit the Centers for Disease Control and Prevention and the World Health Organization.
- Ignore online offers for vaccinations. There currently are no vaccines, pills, potions, lotions, lozenges, or other prescription or over-the-counter products available to treat or cure coronavirus disease 2019 (COVID-19).
- Research before you donate. When it comes to donations, whether through charities or crowdfunding sites, don’t let anyone rush you into making a donation. If someone wants donations in cash, by gift card, or by wiring money, it’s a red flag—don’t do it.
If you follow this advice and your company’s policies about email distribution, you may not fall victim to coronavirus/COVID-19 phishing scams.
In Conclusion
The coronavirus has people on edge. They want to stay up-to-date with the latest news and information, so they may be tempted to click on malicious phishing emails that can compromise your company’s data. Create a template for disseminating information related to COVID-19 and share it with your employees. Make sure they know that any email that deviates from that template should be deleted immediately without clicking a link or downloading an attachment. When in doubt, contact us if you suspect foul play; we can help. In the meantime, stay safe physically and virtually.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.




