COVID-19: Malicious Domains, Malware & Phishing
Crisis breeds opportunity for bad actors. As early as January, attackers were buying domains, building malicious websites, trolling the dark web, and creating phishing scams to steal information and shut down IT networks, including those at critical health facilities.
Buying Malicious Domains
While thousands of domains have been purchased since January 2020, not all of them have been linked to malicious activity, but that doesn’t mean they aren’t or won’t be. Check Point reported the following:
“ Since January 2020, there have been over 4,000 coronavirus-related domains registered globally. . . Coronavirus- related domains are 50% more likely to be malicious than other domains registered at the same period.”
There’s the concern for our physical health, of course, but businesses can’t overlook the threat of malware worming its way into their networks. The most common way for that to happen is phishing attempts that use email to lure recipients into downloading malware. Many of those phishing attempts start with coronavirus-related domains.
Trolling the Dark Web
As if the usual suspects—phishing and malicious code—aren’t enough to keep business on their toes during this pandemic, the dark web is offering hackers exploitive tools. Those goods are flagged with keywords like “COVID-19” and “coronavirus” and targeted specifically to aspiring bad actors.
Some of the goods available to purchase at special rates include “WinDefender bypass” and “Build to bypass email and chrome security.”
Phishing Scams
In an article last week, we explained that “phishing emails appear to be from a trusted source, tricking you into providing sensitive information, downloading malware, or clicking a link to a website that can do either.” In that article, we told you about a fake coronavirus map being circulated via phishing emails that trick you into downloading and running a malicious application that steals information from your PC.
Work-from-home initiatives pose particular phishing threats because remote workers may have a different mindset when working from home. At the office, it’s common to be more aware of the kinds of emails coming through—there’s a certain vigilance about opening suspicious emails or clicking unknown links. At home, though, it’s possible remote employees may let their guard down.
Phishing emails always look and sound eerily similar to well-known organizations like the CDC. Forbes is reporting that “[r]esearchers have already found one malware that was spread via the legitimate-looking email address CDC-Covid19@cdc[.]gov.”
The article goes on to give the following screenshot examples of what to look for in phishing emails.
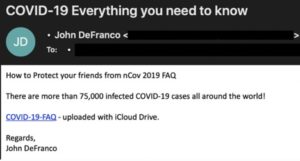
An example of a phishing email with a suspicious link.

It’s a good bet that the attachment on this phishing email will install malware or ransomware that locks you out of your network or steals sensitive data.
We’re all on edge with social distancing and “quarantine in place” directives. It’s normal to want the latest information, and it can be tempting to open suspicious (phishing) emails, click on links that lead to malicious websites, or download attachments promising personal testing kits, masks, cures, or advice.
Train your employees about what to look for to avoid phishing scams. Ensure you have a template your emails follow that your employees can immediately identify as safe.
Targeting Healthcare
Here in the US, Champaign-Urbana Public Health District’s website was attacked by a new ransomware called NetWalker in early March. Ransomware is designed to lock you out of your own computers and network and then demand money for an encryption key. A representative at Simplified Computers of Champaign explained that “NetWalker hides in an essential Windows function to evade anti-virus detection.”
Hackers demanded $475,000 from the health district to regain access to their data. The price was negotiated to $350,000—lower, but we think you’ll agree that it’s not a price you want to pay.
“'[A]ttackers assume emergency-care providers are more likely to pay for files to be restored so they can resume urgent services,’ said Vitali Kremez, head of SentinelLabs, a research division of cybersecurity firm SentinelOne Inc.”
Of course, it’s not just the United States being targeted. University Hospital Brno in the Czech Republic, a COVID-19 testing center, also fell victim to a cyberattack and had to shut down its entire IT network and called for all employees to “immediately shut down all computers due to ‘cybernetic security.’” Two hospitals in the same group—the Children’s Hospital and the Maternity Hospital—were also affected. It’s unknown if coronavirus testing was impacted by this cyberattack.
Protecting Yourself
Malware has always been a problem; it’s just taking advantage of the latest crisis. In most cases, companies aren’t agile enough to make big changes to their cybersecurity on the fly. That’s why we suggest planning ahead even during this current pandemic.
Agio wants to keep your company’s networks and employees safe, so we offer different levels of protection depending on your needs.
Malware is predominantly delivered via email phishing attacks. Our Phishing Protection is a holistic, AI-driven solution to ensure your end users stay protected from the #1 threat—phishing.
A more comprehensive approach to cybersecurity is our SEC Cybersecurity Governance Plan for Financial Services and our Healthcare Cybersecurity 360° Program for Providers and Business Associates. This two-year compliance-focused program is a proactive, methodical approach to cybersecurity, under the direction of a virtual CISO.
Finally, we know nothing is bulletproof, so we offer Managed Detection & Response services. This one ensures you have defenses in place to protect you from anything that gets inside your castle walls.
If you have questions or want to know more about our services, contact us. We’re here to help you in any capacity we can.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.



