PCI 360° Compliance
Payment card data is one of the most commonly breached data types, accounting for an alarming 37 percent of all breaches. With stats like this, it’s more important than ever to deter the bad guys. As a trusted PCI Qualified Security Assessor (QSA), our program addresses PCI compliance for merchants and service providers alike.

Meet Your QSAs
Strengthen your defense.
Our holistic, 12-month programmatic approach to maintaining PCI compliance is rooted in proactive collaboration and CISO-style guidance, with a long-term view towards strengthening your security posture.
PCI Gap Assessment
We determine the likelihood of a cyber-attack by reviewing the maturity of your information security and identifying gaps in your compliance between current security controls and PCI DSS requirements.
PCI Penetration Testing
Knowing how hackers think, we leverage the attacker’s mindset to test and breach your systems both on-site and remotely, successfully identifying weaknesses.
Policy Review Development
We help you write and review your initial security policies, as well as advising on future updates based on changing PCI compliance requirements, external threats, and industry trends.
Incident Response Testing
We facilitate operational- and executive-level incident response tabletop exercises in which we simulate a realistic security incident scenario, allowing for the identification of weaknesses, improvement of response capabilities, and enhancement of overall preparedness for real-world scenarios.
Security Awareness Training
We teach your end users how to recognize and evade a cyber-attack by leveraging your organization’s specific results from our social engineering testing to then tailor a unique annual educational seminar.
Social Engineering Testing
We simulate real-world manipulation tactics used by attackers to exploit human vulnerabilities, such as trust and curiosity, in order to assess your organization’s susceptibility to such tactics and make recommendations on how to educate employees on recognizing and resisting social engineering attempts.
SAQ or ROC Assessment
As a QSA, we assist with the interpretation and response for each requirement and sub-requirement of the Self-Assessment Questionnaire (SAQ) and can perform a formal Report on Compliance (RoC) if one is required.
Proactive Monitoring
Agio monitors your firm’s domain names and public DNS services for unusual activity that may indicate cyber fraud.
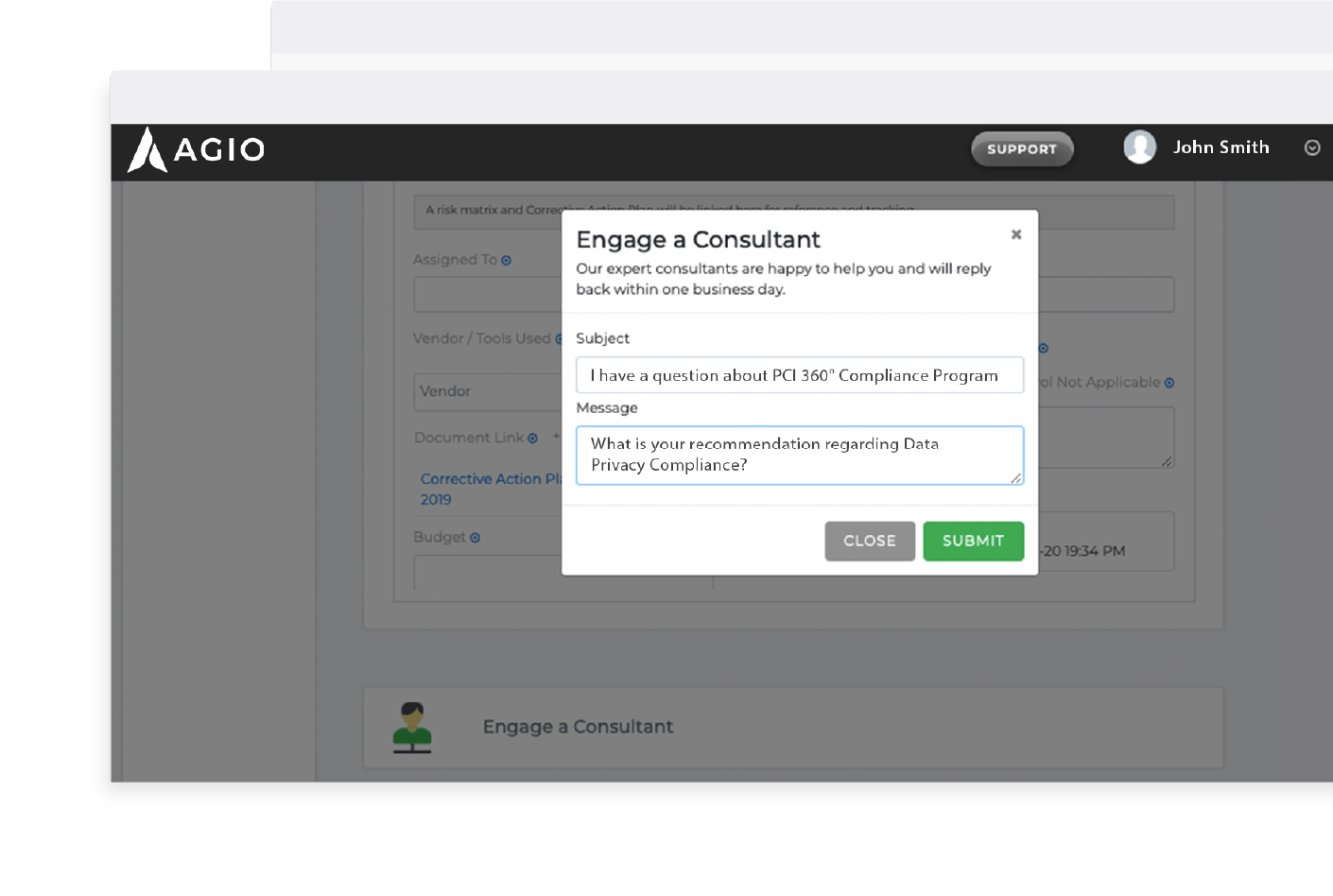
Always-on access to experts & insights.
Your dedicated Project Manager and virtual QSA will host monthly progress reviews to share guidance, updates and strategic recommendations. You’ll get:
- Full access to our software-as-a-service (SaaS) portal
- 360° visibility into the status of your program
- Instant communication with our experts at any time
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.
Trending resources.
Are you in?
Find out whether Agio is right for you. Contact us to design a custom solution for your firm.