Cybersecurity Operations
Cybersecurity to protect your data, your people, and your reputation.
Led by expert security analysts and aligned to the NIST Framework, our Cybersecurity Operations portfolio applies dynamic machine learning to identify unusual behavior and proactively monitor and mitigate threats to your environment.
Your 360° security strategy.
Open Extended Detection & Response
Through dynamic machine learning, we proactively monitor your environment 24x7x365 so you’re never caught on your heels. Our full suite of services fortifies your cyber-defenses and means the difference between a security threat and a security breach.
Incident Response Management
Detection and response have become critical to a robust security posture. We combine prep work upfront with testing and a hacker’s mindset to evaluate and practice your response. So when a breach hits, you’re ready.
Endpoint Detection & Response
Our Endpoint Detection & Response combines the most sophisticated endpoint technology with our 24x7x365 SOC to hunt, investigate, and eradicate attacks before they damage your business. We go beyond no missed alerts and proactively recommend changes to keep your environment more secure. Always.
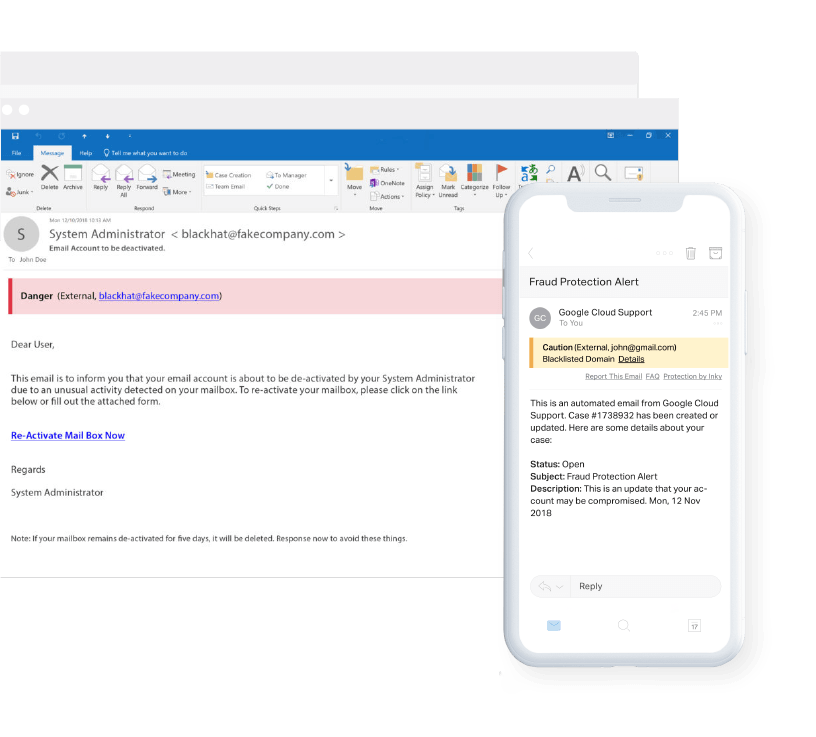
Phishing Protection
We employ with next-gen technology that leverages machine learning and behavior profiling to uncover sophisticated phishing attacks that both trained users and typical email filters miss.
There's more.
Mobile Web Security
To protect your mobile workforce from advanced threats, we offer you visibility while securing traffic both on and off your networks.
Executive Privacy Monitoring
We proactively monitor and report on your executives’ data, email and sensitive files for unauthorized access and anomalies, retaining logs for 12 months.
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.
Trending resources.
Are you in?
Find out whether Agio is right for you. Contact us to design a custom solution for your firm.



