Year in Review: A Three-Front Battle Reshaping Enterprise Cybersecurity in 2024
What started as a typical year of cybersecurity headlines reveals a more complex story — organizations are now facing an unprecedented three-front battle: regulators driving aggressive compliance measures, adversaries evolving at AI speed, and technology innovation outpacing the preparedness to secure it.
As I emphasized during our recent webinar, this increased velocity of change demands that our security controls, risk identification processes, and management frameworks evolve just as rapidly—are you ready for that?
Regulators Demand More Accountability
The regulatory environment has intensified dramatically, with enforcement actions in 2024 estimated at two to three times the volume of previous years in terms of dollar value. The SEC has been particularly active, with its final rule on public companies serving as a roadmap for what’s coming for registered investment advisors (RIAs). SEC regulations now require a four-day incident disclosure mandate, robust risk identification and management protocols, and detailed documentation of how boards are involved in cybersecurity oversight. Regulators outside the US are also buttoning up their requirements, with the EU’s DORA framework introducing additional compliance requirements for organizations operating globally.
The most successful organizations demonstrate a clear link between senior leadership engagement and security effectiveness. This involvement signals the importance of security throughout the organization and helps ensure appropriate resources and attention are allocated to addressing security challenges.
Adversaries Evolve at AI Speed
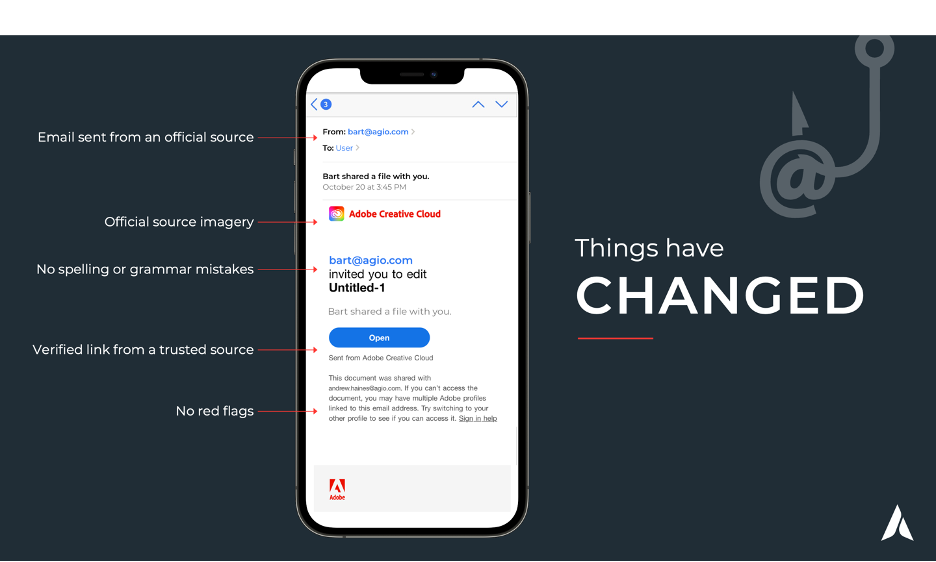
Bad actors have radically transformed their tactics, weaponizing artificial intelligence (AI) to create increasingly sophisticated attacks that are harder to detect. For example, traditional phishing detection methods, like spotting poor grammar or generic greetings, are becoming obsolete. With AI, attackers can craft highly personalized messages with devastating effectiveness. The math is simple but alarming: when an email contains three or four personal data points—like your name, credit card type, card number, and frequently visited vendor—success rates can reach 50-70%. For every two targeted emails, attackers are likely to succeed once.
While social engineering remains the primary attack vector, technical vulnerabilities have emerged as an increasingly serious threat. The path of technical vulnerability exploitation has increased by 180%, with web applications becoming the second most common entry point. This surge is partly driven by AI tools that can scan open-source software for vulnerabilities—not just identifying them but providing instructions for patching and exploitation. The risk extends beyond publicly available AI models like GPT or Claude; threat actors download open-source models and strip out their safety controls, creating more dangerous tools.
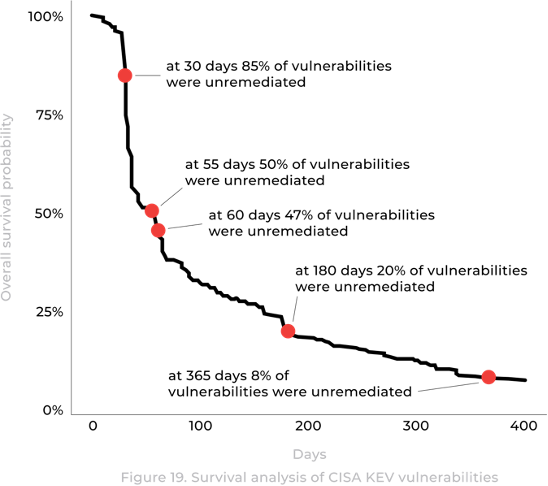
Poor patching practices compound this technical vulnerability problem. Even in technology-managed systems, 8% of known vulnerabilities remain unpatched after a year. For systems not managed by technology teams, this figure jumps to around 30%. The issue is more than missing patches—firms often fail to monitor their patch status, understand how many devices remain vulnerable, or grasp the level of risk involved.
Technology Outpaces Preparedness
AI is helping generate code daily, ramping up the momentum of changes that security teams must track and manage. API traffic has exploded to become the dominant form of web traffic, and what appears to be a single API endpoint might contain hundreds of execution paths. Most organizations struggle to maintain and manage a comprehensive inventory of the API endpoints they use and publish.
Managing vendor platforms adds another layer of complexity. Take Microsoft, for example. They’ve released numerous code updates, features, and capabilities this year alone. Firms must now track what’s being released and what’s being added or removed, understand best practices, and determine recommended settings. A single anti-spam and anti-phishing system like Inky can have over 40 different configuration settings that need to be tracked in a Configuration Management Database (CMDB), optimized, and monitored for changes., optimized, and monitored for changes.
In response, forward-thinking firms are establishing structured schedules for risk management: real-time monitoring for critical system alerts, daily security event reviews, weekly vulnerability scanning and patching, monthly configuration reviews, and quarterly or semi-annual deep-dive operational business risk reviews. However, these processes only work if companies act on their findings and maintain clear documentation of their risk management decisions.
The challenge isn’t just about keeping up with the technology—it’s about scaling your protections, controls, and risk management capabilities at the same pace your technical environment grows. As your system endpoints, device endpoints, and API endpoints multiply, the question becomes: are you positioned to manage this growth effectively?
Looking Ahead
Organizations today find themselves in what I call a “vice grip”—compliance mandates squeezing from above, bad actors and threats pressing from below, and technological advancement creating pressure from all sides. It can be overwhelming. I notice a lot of firms struggle to maintain the knowledge, capability, people, time, and budget to address their current challenges, let alone prepare for future threats.
Successful organizations will be those that recognize where they are in this cycle and actively prioritize and address the multi-faceted layers of our security landscape. Firms must establish a cadence of identification and management across their regulatory obligations, third-party relationships, and operational risks. They need to shift from passive acknowledgment of risks to active management, with clear documentation and communication of all decisions.
For more insight, please watch my webinar or contact us today.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.




