The Evolution of Brute-Force Attacks: Protecting Your Firm’s Remote Access
Some cyber threats never truly disappear; they simply adapt. Brute-force attacks, one of the oldest techniques in the cybercriminal playbook, have undergone a significant transformation that demands attention from firms of all sizes.
Last week, we hosted an AgioLive on LinkedIn with Chris Schoenwetter, Director of Cyber Operations, and Rick Kurtz, Associate Director of Cyber Operations, to discuss the unprecedented risk brute-force attacks pose to virtual private networks (VPNs) and the remote access infrastructure that firms rely on for daily operations. You can read the highlights below.
Recognizing the New Face of an Old Threat
Historically, protecting against brute-force attacks was straightforward. Security teams could identify and block a handful of suspicious IP addresses making repeated login attempts. Today’s attackers leverage botnets, compromised devices, and automated tools to rotate through millions of IP addresses, making traditional defense strategies obsolete and potentially exposing firms to significant operational, reputational, and regulatory risks.
Moving Beyond Traditional Security Approaches
Modern protection requires a strategic shift in how firms approach remote access security. Cloud-based identity providers have emerged as a crucial defense layer, offering several advantages over traditional security measures:
- Proactive threat screening before authentication attempts reach your infrastructure
- Automatic identification and blocking of malicious IP addresses
- Access to extensive threat intelligence networks that protect against emerging threats
Additionally, implementing a zero-trust model fundamentally strengthens your security posture by:
- Restricting authenticated user access to only necessary resources
- Requiring verification for every access attempt
- Limiting potential damage even if credentials are compromised
Before investing in new security tools, though, firms should conduct a thorough audit of their existing security stack. Many organizations already have robust security capabilities, including multi-factor authentication, built into their current platforms—they just need proper configuration and optimization. This approach helps eliminate redundant security tools, maximize existing platform capabilities, manage costs effectively, and streamline security operations.
Building & Measuring a Sustainable Security Program
Implementing strong security controls is only the first step in developing a robust security program. Success requires both a well-orchestrated operational approach and clear metrics to validate effectiveness and drive continuous improvement. A comprehensive security program focuses on both foundational controls and ongoing measurement.
For the foundation, organizations should focus on three core operational elements:
- Security Control Inventory. Maintain a comprehensive understanding of your security landscape by documenting all security controls and their purposes, identifying overlapping capabilities, regularly auditing configurations, and ensuring tools deliver their intended value
- Configuration Management. Strengthen your security foundation through detailed documentation of security settings, regular validation of control operations, continuous updates to maintain effectiveness, and proactive gap identification and remediation.
- Monitoring and Auditing. Maintain visibility into your security posture with comprehensive system logging, regular security event reviews, continuous validation of control effectiveness, and proactive threat identification and response.
To ensure these foundational elements remain effective, firms must implement clear metrics that provide actionable insights:
- Authentication Metrics. Monitor failed login attempts, account lockouts, and geographic sources of authentication requests to identify potential attack patterns and adjust defenses accordingly.
- System Performance. Track VPN and authentication system performance to identify potential security events before they escalate into significant incidents.
- Security Control Effectiveness. Regularly audit security configurations and measure control performance against intended design to ensure comprehensive protection.
By combining robust operational controls with meaningful metrics, organizations can build and maintain a security program that adapts to emerging threats while providing clear visibility into its effectiveness. This data-driven approach ensures security investments deliver measurable value while enabling continuous improvement of the overall security posture. Regular assessment and refinement of both controls and metrics creates a dynamic security program capable of meeting today’s challenges while preparing for tomorrow’s threats.
Proactively Manage Security Risks with AgioNow
Agio’s Risk Register, accessible through the AgioNow client portal, serves as your command center for cybersecurity risk management. It consolidates findings from various security sources—assessments, vulnerability scans, penetration tests, and more—into a comprehensive view of your security posture. This centralized approach helps identify vulnerabilities that could be exploited by sophisticated brute-force attacks, enabling your team to efficiently prioritize remediation efforts, track progress on security initiatives, and demonstrate regulatory due diligence.
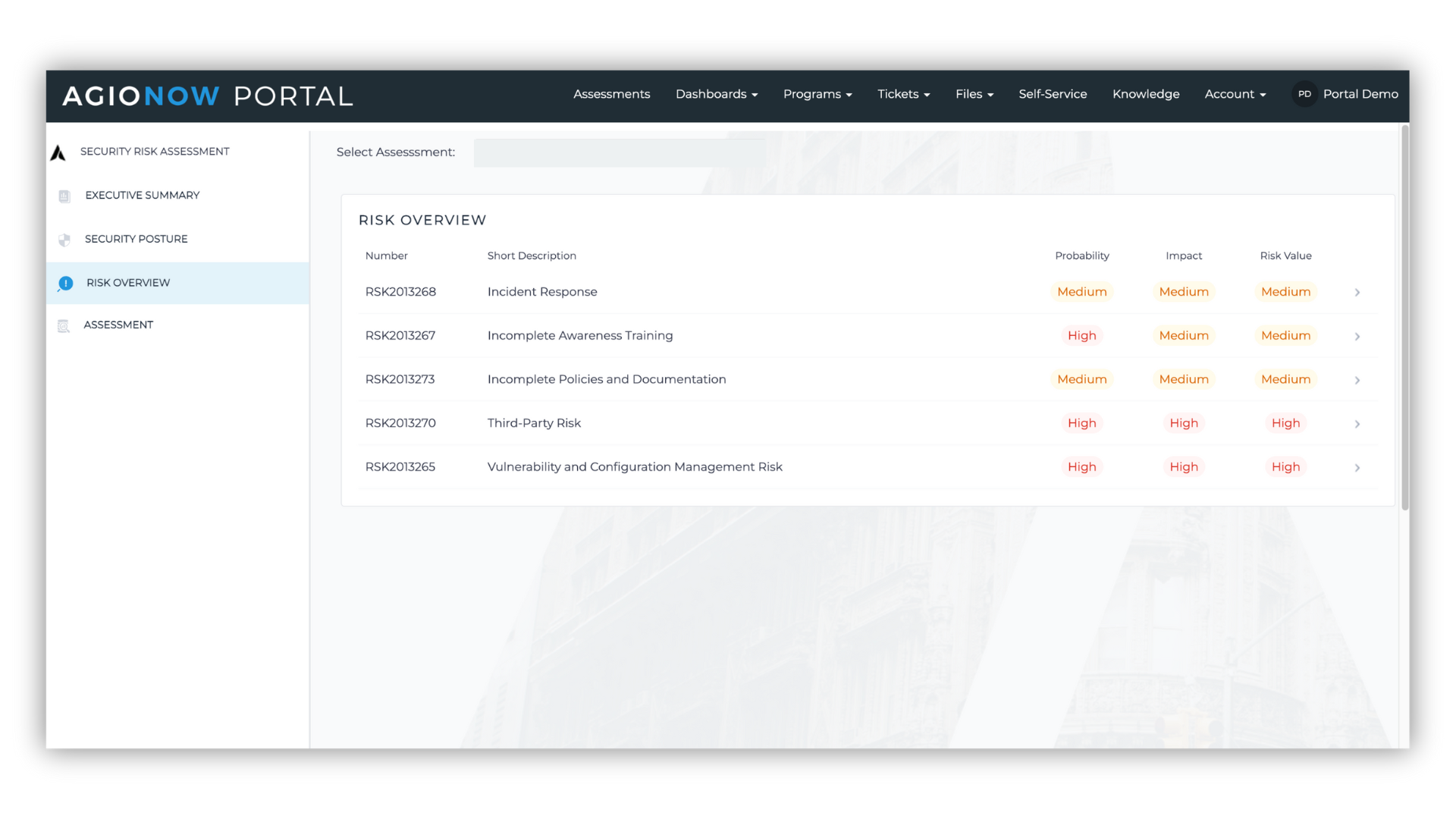
Working alongside the Risk Register, Agio Foundations conducts nightly automated comparisons of your security policies against industry best practices. When it identifies nonstandard configurations or security gaps in authentication systems that could enable brute-force attacks, Foundations automatically creates actionable entries in your Risk Register. An optional auto-healing feature can remediate issues automatically, reducing your security team’s workload.
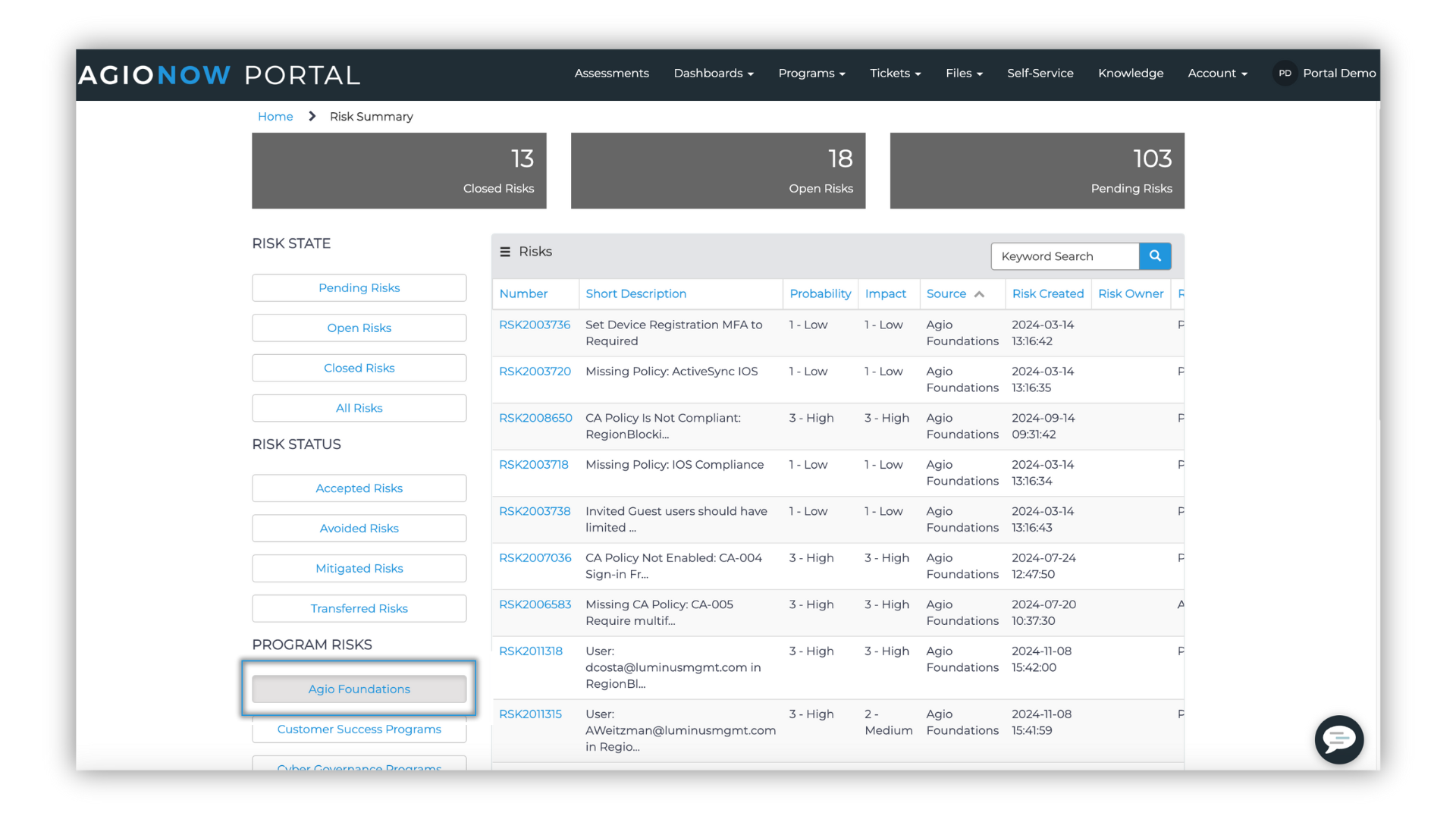
Together, these integrated tools transform security from reactive firefighting to proactive protection—precisely the strategic shift needed to counter modern brute-force attacks targeting remote access infrastructure.
Taking Action
The evolution of brute-force attacks has prompted a fundamental shift in how firms must adapt their security strategies to address these sophisticated threats while maintaining operational efficiency. Success requires more than implementing new tools—it demands a comprehensive approach that combines modern security solutions with proper configuration, continuous monitoring, and regular validation. By taking a proactive stance on security and implementing these strategies, firms can better protect their operations, maintain client trust, and ensure regulatory compliance.
For more insight on brute-force attacks, please watch the LinkedIn Livestream Replay.
If you’re ready to strengthen your security posture with clear visibility and actionable insights contact us to learn how our Risk Register and Foundations can enhance your cybersecurity program.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.




