The Watch Commander’s Log for May 6th, 2020
This is the first in a series of technical articles from The Watch Commander’s Log. In them, we provide a direct view into the details of some of the threats Agio’s Managed Detection and Response (MDR) team handles for our clients—on an anonymized basis, of course. If you have questions about anything you read here, please feel free to reach out to us at mdrbriefings@agio.com. If you are a current Agio MDR client, you can also reach out to your assigned MDR analyst.

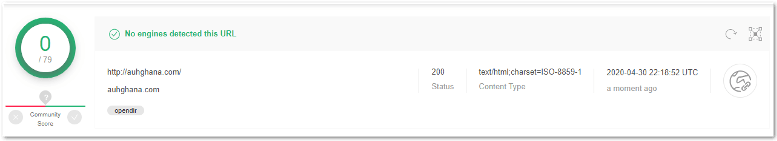
Agio received reports of a credentialed email harvesting site (hxxp:\\auhghana[.]com) targeting its customers. The MDR team gathered the phishing kit and broke down the components.
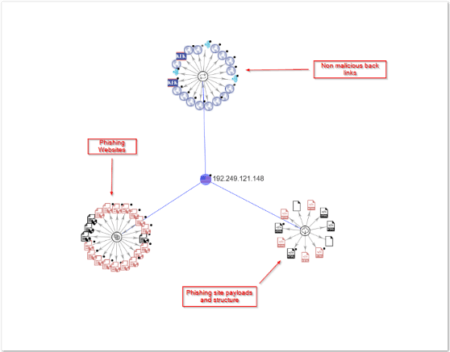
VirusTotal doesn’t flag this site as malicious because the api.php is customized to avoid detection. The graph provided by VirusTotal shows the attacker’s backend infrastructure and the associated files and sites related to this specific phishing email campaign.
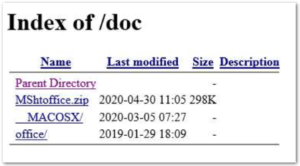
This is the Apache directory of the phishing site. Attackers leave these phishing kits open to the public to allow quick changes to landing pages and faster administration of attacks against potential victims. They’re clearly not security people because they’re using low-level tactics, and they aren’t worried about being blocked. They’re focused on having plenty of targets and being able to rotate phishing kits to make the most profit quickly.
To gather the attacker’s scripts and information, we extracted the .zip file contents from a packet capture in Wireshark.
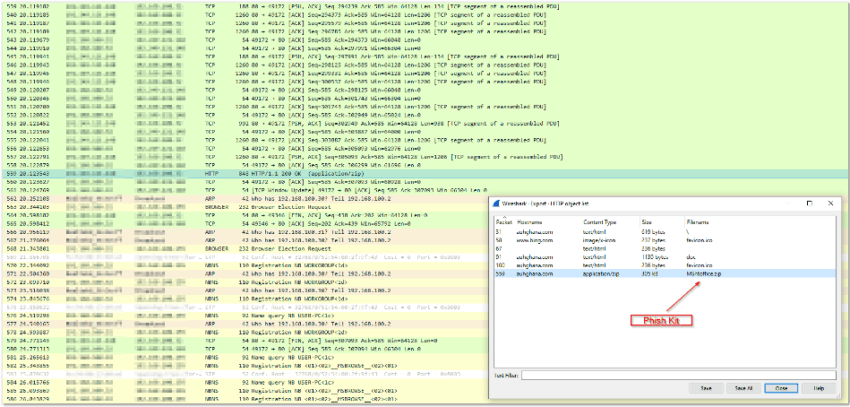
As you can see by the extracted files, there’s an OSX version and a Windows version, giving the attacker as wide a net as possible. We’ll walk through specific sections and the purpose of the individual php files below.
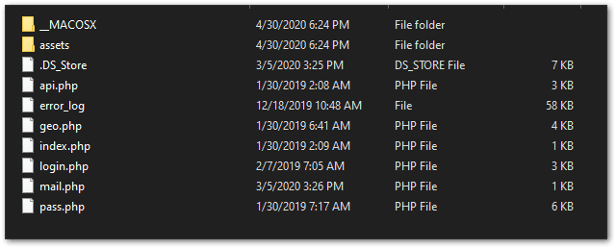
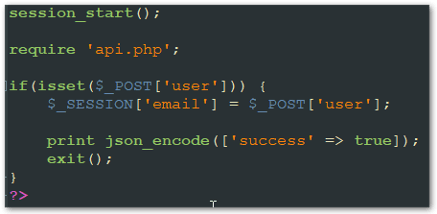
Login.php – Posts the output of the attack to an encoded JSON file and uses the MaxMind geolocation database to gather location information from the victim.
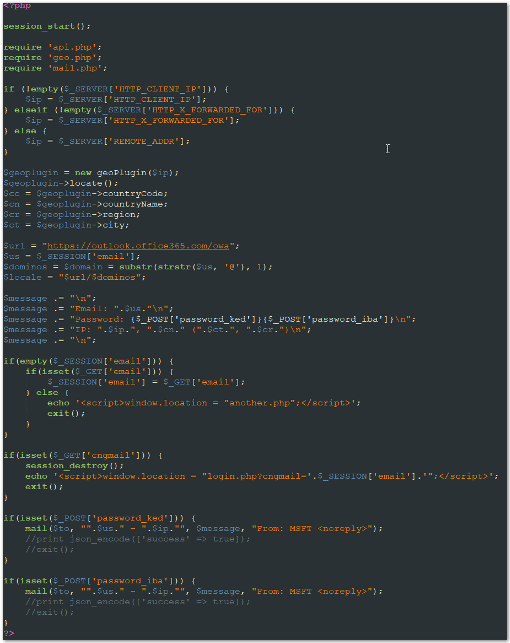
Pass.php – Passes the correct parameters to mimic an Office 365 login splash page, then parses the input to pass to the login.php script.

Geo.php – Allows the attacker to be selective about the display of the compromised website based on the longitude and latitude of the victim’s machine. This is used to avoid compromising users from the attacker’s host country or other targets that aren’t in scope.
Mail.php – Passes hardcoded email accounts to gather the encoded JSON output of the login.php script. This is how the data is exfiltrated to the attacker.
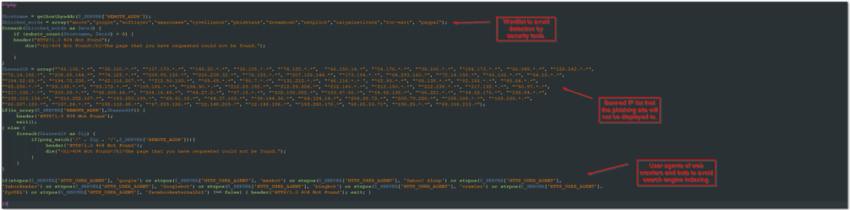
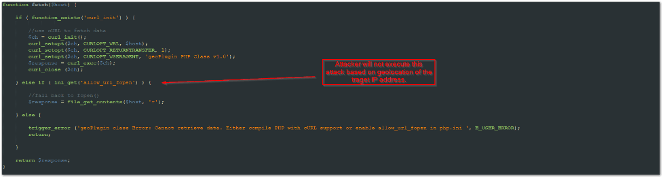
Api.php – A list of user agents, IP addresses, and words to avoid web crawlers and detection by open source security tools.
This is a classic example of a phishing campaign that can target any industry. Identification of patterns in these phishing attempts leads to better detection methods. Understanding the method and structure of a potential compromise allows a defender to gain the edge.
If you have questions about anything you read here, please feel free to reach out to us at mdrbriefings@agio.com. If you are a current Agio MDR client, you can also reach out to your assigned MDR analyst.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.

