Cybersecurity Governance Best Practices
Though cybersecurity professionals warn against it, many financial services firms tend to treat cybersecurity governance as a regulatory check-the-box instead of viewing it as essential to maintaining secure, reliable, and resilient information systems. Even as threats become more sophisticated and prolific, many organizations opt for the minimum safeguards—believing a cyber event won’t happen to them—rather than building a holistic mature cyber governance function.
We can’t emphasize this enough: cybersecurity isn’t a compliance issue; it’s a risk issue. Checking a box doesn’t mean your data is safe. But when you flip the script and invest in holistic protection of your people, systems, and data, you’ll be safe and compliant.
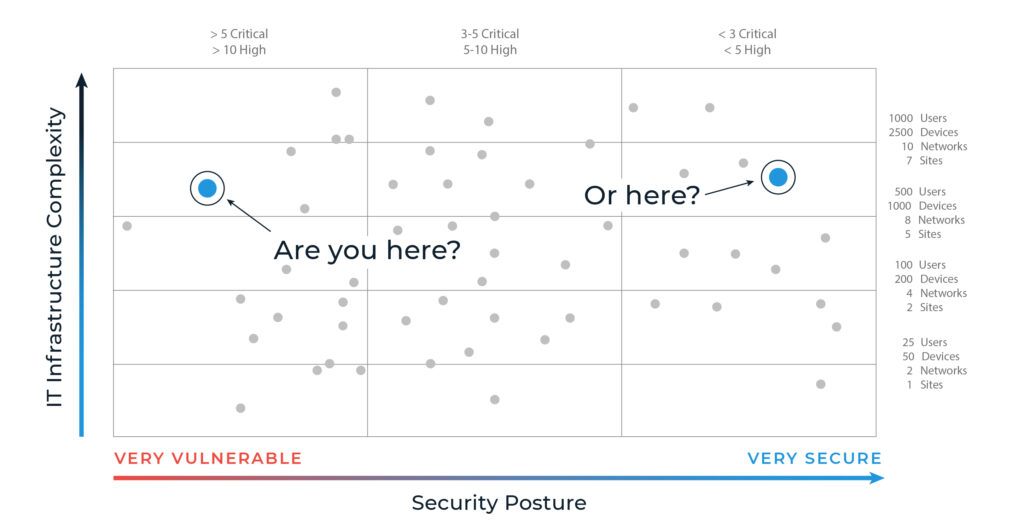
It seems obvious, so why aren’t more firms doing it? Robust cybersecurity governance requires time, money, and effort, and adds complexity to IT management. It’s a cost center, not a profit center. That is, until they suffer a ransomware incident and discover just how costly a lack of cybersecurity can be financially and reputationally.
The path to a more secure cyber posture requires a strong partnership with a someone who understands your struggles, can help you secure your data while keeping an eye on the regulatory landscape, and, most importantly, can help you chart and measure the course to achieving a mature cyber operating model. That’s where Agio’s Cybersecurity 360 Governance Program comes in.
If you think of your journey linearly, your trajectory from left to right tackles increasingly complex security milestones. We guide you every step of the way to ensure hardened security and rock-solid compliance.
Here’s what the journey with Agio looks like:
- The first stop on our journey is ownership of the problem. Your initial security risk assessment (SRA) uncovers the basics your firm must address to create the foundation of your security efforts. You’ll work on refining responsibilities and assigning those to the right people; implementing the right policies; and developing and executing processes that ensure your people, systems, and data are secure. The growth between this level and the next will be significant. We call it the first big move in the right direction!
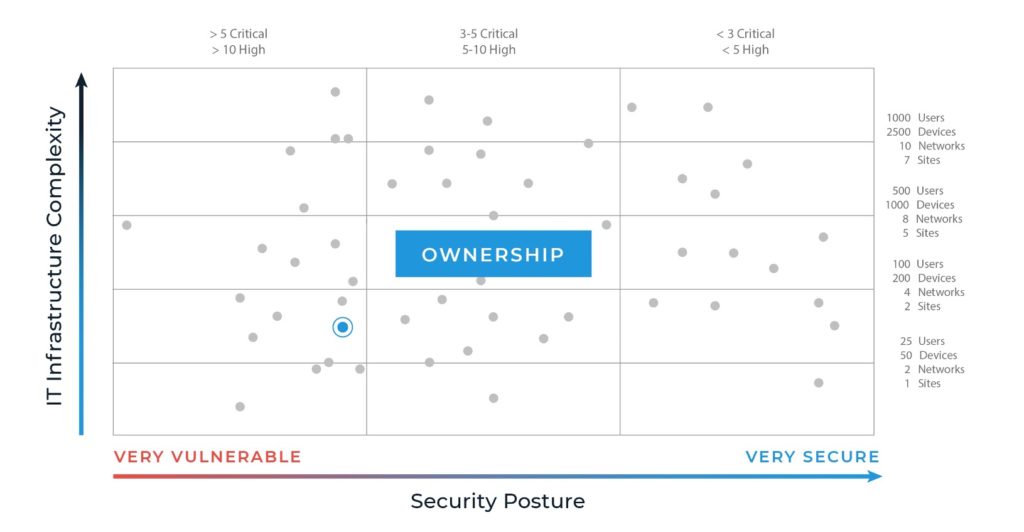
- After that, you can focus on control. As your organization begins to develop a mature cyber governance model, you tackle more complex security issues like vendor management, access control policies, regularly reviewing and amending controls, and establishing data classification and loss prevention standards.
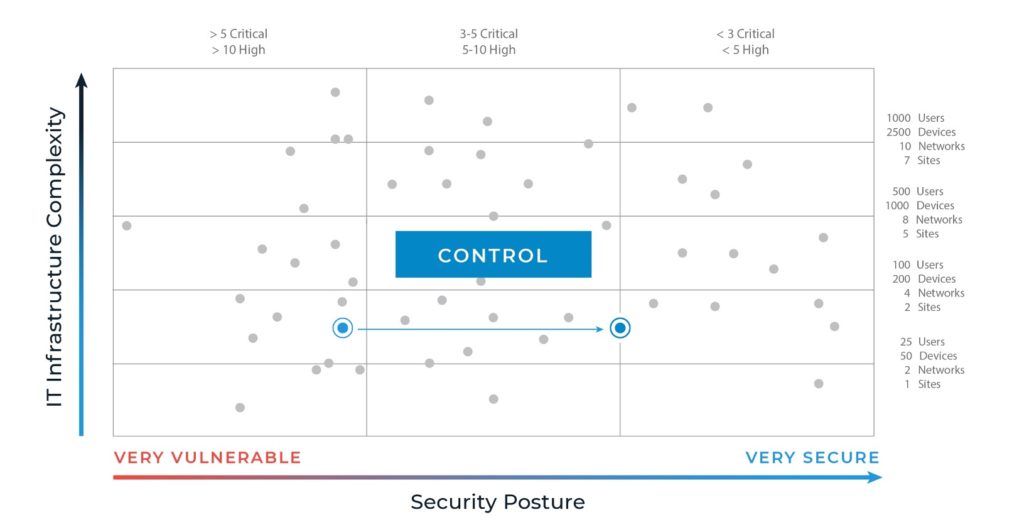
- Only then can you claim a mature cyber governance model. At this point, your organization will have established and fortified the more complex cybersecurity requirements in the Control phase by addressing acute findings. For example, if outdated software is integral to a core process, you’ll work on finding a way to move to an updated system without losing functionality or data.
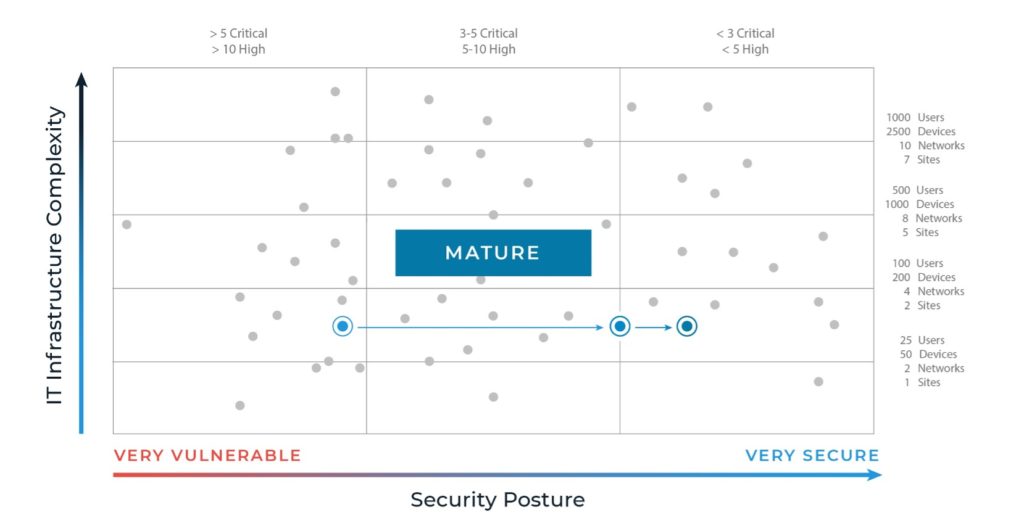
- Continue to fortify your safeguards. Cybercrime is escalating at a prolific rate. Without the resolve to diligently revisit your policies and continuously fortify your systems and data, it’s not a question of will you lose ground but how much ground you’ll lose. As the threat landscape shifts, are you agile enough to evolve with it? Sustaining a mature cybersecurity posture depends on recursive oversight and testing (e.g., yearly pen tests, social engineering exercises every few months, assessments every two years, etc.). Without persistent attention, you risk losing ground and becoming vulnerable.
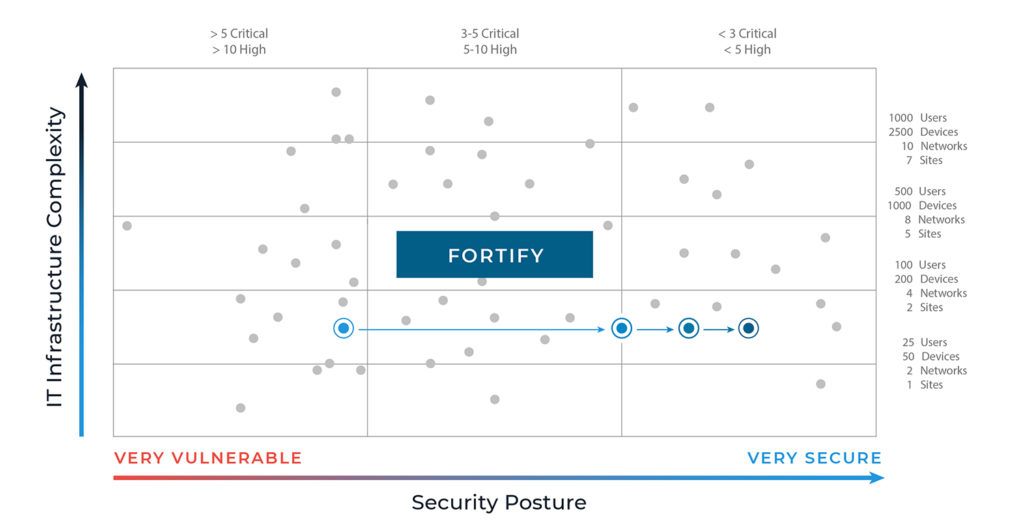
Protecting yourself against financial and reputational pain requires a long-haul plan focused on risk prevention that leads to compliance, not the other way around. Every move to the right is measured against your cyber-strength performance benchmarks and those of your peers. Each milestone conquered confirms your investment in and commitment to security.
Agio’s Cybersecurity 360 Governance Program provides straightforward, measurable tasks that bridge the gap between security and compliance, so you’re prepared for worst-case scenarios. Find out more.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.




