More Stringent PCI Requirements and Complexity Coming March 2024
For merchants and service providers accepting digital payments, staying compliant with the Payment Card Industry Data Security Standard (PCI DSS) is a must.
However, after March 31st, 2024, significant updates to the PCI DSS take effect, bringing more complexity for merchants and service providers. At Agio, our experts are always tracking changes to enable merchants and service providers to identify gaps between current security controls and PCI DSS requirements, develop a roadmap for remediation, and complete your annual assessments.
What’s Changing with PCI DSS v4.0
With PCI DSS v4.0, there is a shift to a zero-trust approach. Simply attesting to periodic activity like penetration testing or security awareness training is no longer enough. Entities need to demonstrate explicit, documented evidence that these and other recurrent requirements actually occur in line with PCI’s guidelines. Key additions include more rigorous vulnerability scanning, additional multi-factor authentication requirements, protection of pre-authorization sensitive authentication data, targeted risk analyses, and greater protection and management of payment pages.
For example, merchants and service providers will now have to provide detailed documentation that security awareness activities occurred on specific dates, which employees completed them, what the training encompassed, and who approved the content. Similar granularity applies across all periodically performed processes under PCI DSS v4.0.
Expanding Scope of Penetration Testing and Vulnerability Scans
PCI DSS v4.0 also newly requires merchants to conduct penetration testing and vulnerability scans from inside your network. For example, with the new requirement, any penetration testing, or vulnerability scans should be conducted behind an internet-facing virtual private network (VPN). With remote work continuing across financial services, securing external connectivity has become a heightened concern.
Meanwhile, service providers will have to demonstrate added vigilance around detecting cardholder data in logs and awakening new requirements around securing credentials and minimizing unnecessary data retention.
For a full list of changes, please visit the PCI SSC’s Document Library to download a Summary of Changes.
What Happens if I Don’t Comply?
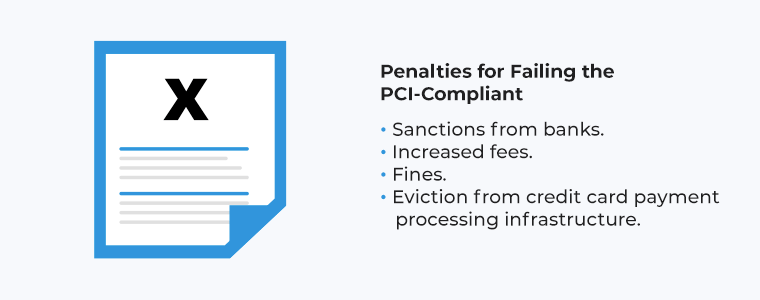
You might ask – what’s the consequence of lagging or only partially meeting the PCI DSS controls? How does non-compliance impact my relationship with payment processors and card brands? Does non-compliance come at a cost?
Unfortunately, the short answer is yes — lack of strict PCI DSS compliance can directly hit your bottom line. Even before version 4.0 added these extra requirements, staying fully compliant was already tough for a lot of merchants and service providers, given the hundreds of requirements. The costs can vary, depending on the violation, the allotted time you continue to violate, and if there was a breach.
Now, what’s the damage if assessments reveal partial or full non-compliance? Beyond shaking the trust you’ve built with your processor and card brands; they can impose tough financial penalties. And if insufficient progress towards full compliance draws fines over longer periods. Ultimately, brands can go as far as permanently cutting off payment processing altogether for serious repeat violations — a nightmare scenario for revenue.
So in short — letting PCI obligations, old or new, slip through the cracks introduces major monetary risks and relationship impacts that cut straight to the core of operations. And while the exact consequences may differ, preventing such incidents is paramount.
But you don’t have to go through it alone. Agio is equipped with the right knowledge and experts, with over a decade of experience, to keep you from reaching that point.

How do I Prepare for PCI DSS v4.0?
Given the substantial financial and reputational risks of not meeting PCI DSS requirements, whether long-standing or newly introduced, the time is now for merchants and service providers to get prepared. Yet adhering in full can be overwhelming, especially for smaller firms lacking specialized IT and compliance resources.
When it comes to getting up to speed on these new PCI standards, we always recommend going straight to the source. The PCI Security Standards Council’s website has a wealth of in-depth resources that break down all the nitty-gritty details on what’s changing and how to prepare.
Additionally, be sure to check out the Council’s Document Library, where you can download a Summary of Changes. This piece lays out a helpful side-by-side comparison that spells out exactly what merchants and service providers like yourselves need to do to comply with the updated requirements.
Reviewing those materials is the best first step to get yourself and your teams educated. Forewarned is forearmed, so having that PCI knowledge under your belt ensures you fully understand the regulatory expectations and can plan your compliance efforts accordingly.
At Agio, we know it can be daunting, intimidating even, to sift through a 40-page document whenever a new standard or regulation comes out. That’s why we have the right guidance and tools in place to make PCI compliance easier for you.
What Options Do I Have?
Leveraging managed IT and cybersecurity providers like Agio makes the difference. We lift the compliance burden through holistic offerings spanning advisory, design, documentation, testing validation, and remediation based on our deep bench of dedicated PCI compliance experts.
As a Qualified Security Assessor (QSA) for over a decade, Agio has always followed stringent documentation standards, even before PCI announced requirements for detailed proof. We believe comprehensive documentation and due diligence are key, and clients can trust that we do our due diligence both in the past and moving forward.
Agio evaluates primary compliance domains like securing systems/networks, protecting stored data, encryption, access controls, monitoring, and policy enforcement. We further help merchants scope cardholder environments correctly – which categorizes required compliance activities.
But we don’t just assess – our compliance team advises security roadmaps and partners long-term to ingrain required controls. We provide expert resources to not only get in compliance but stay in compliance amidst shifting demands.
Here’s how Agio delivers 360 degrees of PCI support:
- QSA-Style Guidance: Our primary QSAs educate clients on PCI DSS obligations both current and emerging while providing strategic roadmaps tailored to infrastructure maturity, budget, and risk tolerance. We erase ambiguity around new standards through personalized guidance.
- Testing & Validation: Leveraging certified PCI assessment professionals and SaaS platforms purpose-built to collect compliance evidence, Agio thoroughly audits cardholder environments against applicability statements. We validate security controls through methods like vulnerability scanning, penetration evaluations, firewall reviews, and device analysis while ensuring proof documentation.
- Remediation: Where deficiencies surface within clients’ cardholder data spheres, our team prescribes precise tactical remediation plans accompanied by implementation support to attain compliance. We stand ready to help refine policies, tighten configurations, monitor infrastructure, and enact all necessary adjustments to clear audit findings based on intimate knowledge of DSS controls.
- Reporting & Documentation: As a QSA, we’re here to help you make sense of each requirement and sub-requirement in the Self-Assessment Questionnaire (SAQ) and offer support in crafting your response. If you need it, we can also take care of preparing a formal Report on Compliance (RoC). We provide the needed operational and technical documentation detailing compliance activities centralized within our system that also facilitates efficient audits.
- Ongoing Advisory: We partner beyond point assessments to provide continuous advisory aligned to clients’ PCI compliance roadmap covering activities like risk classification adjustments, emerging control requirements, infrastructure developments, newly applicable best practices, and updated card brand guidance.
Our extensive experience spanning complex merchant environments and service provider ecosystems translates into tailored strategies and acceleration support for addressing PCI DSS v4.0 changes head on. We communicate fluently between technical, operational, and executive stakeholders while providing transparency every step of the way.
Invest in Peace of Mind Amid PCI Complexity
Don’t go it alone – a data breach resulting from PCI compliance shortcomings can spark immense financial damage stretching into six-plus figures and wreck consumer trust.
Turn to Agio’s PCI 360 Compliance Program for end-to-end guidance adhering to and benefiting from PCI DSS v4.0 while insulating your financial services organization from risk. Investing in robust security fundamentals pays dividends across cyber resilience, partner trust, operational efficiency and ultimately long-term profitability.
Contact Agio today to schedule your PCI gap assessment and roadmap consultation.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.