White Paper |
Managed SIEM v. MSSP v. MDR: What’s the Difference?
When a client goes to market to find security monitoring services, they find three kinds of providers, and this white paper walks you through what you can expect from each.
1. Managed SIEM (Security Information & Event Management)
These providers host a SIEM platform. The provider stands up an instance of the SIEM and integrates whatever logs happen to be readily available. The client becomes a direct recipient of whatever alarms and reports the SIEM provides. It is up to the client to understand what the alarms mean and what to do about them. There’s little, if any, analysis by the provider. The choice of what logs get integrated is a matter of convenience, not value. This tends to be the lowest cost option. If the client happens to have a mature security team, it may be a good option. For clients that lack dedicated intrusion analysts and IR staff, Managed SIEM services are insufficient at best. At worst, they offer a short-term false sense of security at a low cost.
2. MSSP (Managed Security Services Providers)
MSSPs often host the SIEM, but sometimes the SIEM is co-managed—the client hosts it in their environment, but the MSSP maintains it. This provides a higher degree of control by the client, but it creates major operational headaches for the provider. Lack of standardization across clients creates higher operational costs and severely limits the provider’s ability to scale engineering and attack detection. MSSPs that host the SIEM, on the other hand, are better able to scale and tend to be more successful at detecting attacks.
What MSSPs (and Managed SIEM providers) lack are hunting and integrated IR (Incident Response). Hunting is a process that begins when a highly skilled analyst dissects a common threat. They identify indicators like malicious IP addresses, URLs, domain names, file hashes, processes, and attack patterns. Rather than simply feeding these into the SIEM and waiting for alarms, they reach back into the SIEM (or security data lake) and search for known TTPs (Tools, Techniques, and Procedures) that would lead them to signs of a successful attack, or one in progress.
Examples of Hunting
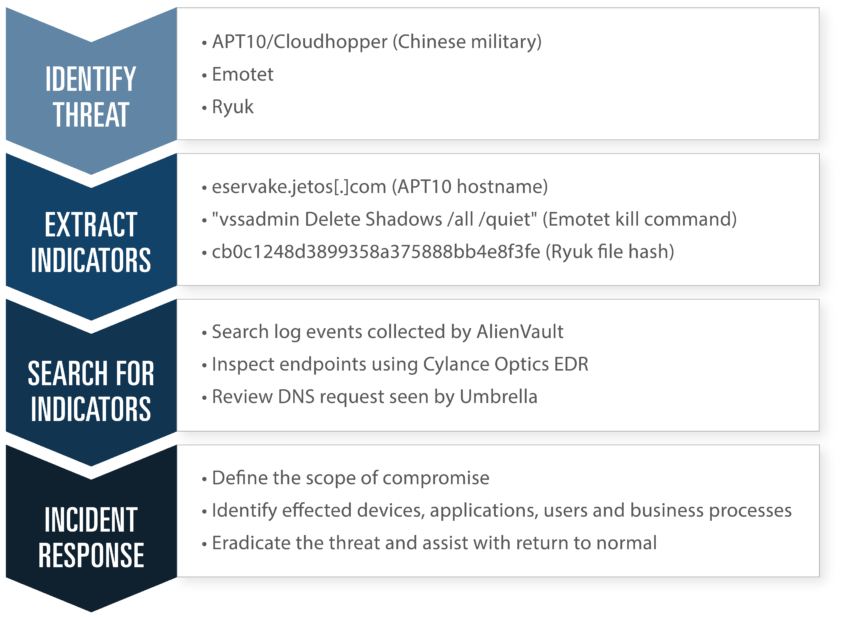
MSSPs tend to offer IR, but only as an add-on contract. Normally, an MSSP will sell a retainer for services to be delivered as needed. There is no IR planning, no tabletop, no policy development, and no testing of the incident response process. When the IR service is sold as an hourly retainer, there is little incentive on the part of the MSSP to help the client avoid incidents. Should an incident occur, the clock starts ticking and the MSSP’s incident handler bills against the retainer. And because the IR specialist is not part of the MSSP operations team, they lack familiarity with the client’s environment, technology, people, culture, and business. An MSSP incident handler walks into every incident cold, and therefore must spend precious time orienting themselves to the client’s business.
3. MDR (Managed Detection & Response)
As an MDR provider, our goal is to find malicious hackers, then get rid of them. Many MSSPs and Managed SIEM providers falsely employ the MDR brand. In addition to providing a SIEM, an MDR provider like Agio offers a comprehensive set of technologies and services. These include a well-tuned, carefully chosen set of technologies, such as Cylance Optics, AlienVault, and Cisco Umbrella. An MDR provider also places hunting at the center of their analysis, prioritizing finding IOCs (Indicators of Compromise) over merely fielding incoming SIEM alarms. Incident response works best when it is closely integrated with security monitoring. Operationally, it enables familiarity over time between the MDR provider’s staff and the client’s internal team. It provides the continuous development of the client. Having a high degree of familiarity between an MDR incident responder and the client means that when incidents occur, they can be dealt with more quickly, more efficiently, and with less risk of errors that may occur due to a lack of mutual understanding.
Another advantage of integrating incident response services with MDR is that doing so creates a natural incentive for the provider to catch and contain incidents as early as possible. Because IR is built into the MDR service, there is no incentive to exhaust a retainer. When an incident occurs, Agio’s MDR team “owns it.” Our client’s pain is aligned with our pain. We strive to find attacks early because doing so means fewer sleepless nights. In MDR, time and attention are scarce commodities. The average MDR analyst is rarer and more expensive than ones that tend to staff MSSPs. A typical MSSP is structured in three tiers, where the Tier 1 analysts filter alarms and forward certain ones for analysis by more highly skilled analysts. Tier 2 analysts forward complex and high-priority alarms to a small group of highly skilled Tier 3 analysts. This sort of system assumes that the SIEM is consuming all necessary logs, that it generates highly accurate alarms, and that the Tier 1 analysts don’t overlook sometimes subtle details. The top of the three-tier model is entirely dependent on the SIEM and the two subordinate layers that precede it in the chain of alarm hand-offs. The problem with this model is that the least skilled (cheapest) analysts are required to act as a filter for the most skilled (expensive) ones.
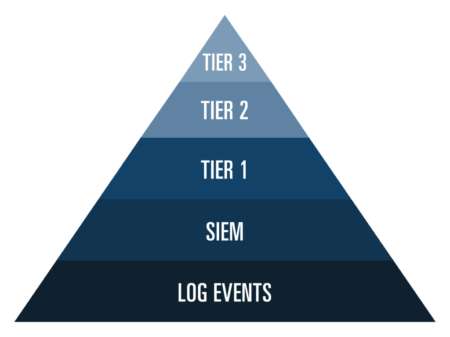
In the MSSP inverted funnel model, Tier 3 analysts are few in number and are dependent on tier 1 analysts, who are least able to catch attacks.
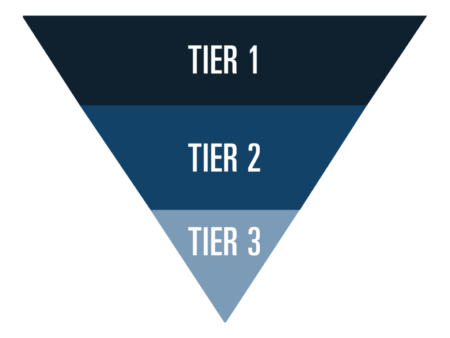
Agio MDR employs a flat structure, where all analysts perform triage, incident response, and sometimes platform engineering.

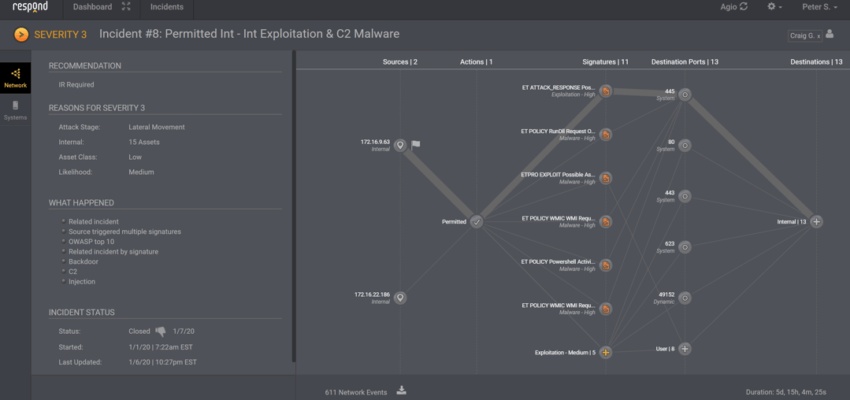
This presents a problem: how do we triage large numbers of log events while leaving time and brainpower to hunt and analyze? The answer is Robotic Decision Automation (RDA) provided by Respond Analyst from Respond Software. Respond Analyst employs artificial intelligence that mimics the actions of a highly-skilled SOC analyst, with two crucial differences. Humans have a short-term memory capacity of 5+/-2. Therefore, at best, an analyst can keep about a half dozen facts in their mind, correlate them and reach a conclusion. Humans also have limited work hours. On any given day, an analyst spends about 5 hours doing triage and analysis, with the remaining 8 hours on administrative matters, conversations with clients, training, threat research, and other tasks. That means they lack visibility of 19 hours per day, barring notes carefully recorded and handed from one shift to the next.
Respond Analyst has virtually unlimited memory and no need for sleep, training, PTO, or other such human needs. It can observe millions or even billions of security events across days, weeks, and months. Respond Analyst can detect subtle and novel attacks. Because it is aware of event patterns, it is not necessarily dependent on individual SIEM rules. Respond Analyst replaces the Tier 1 layer function with capabilities that no person or team could ever have.
The results are:
- Earlier detection of attacks
- Detection of subtle and novel attack patterns
- Less time spent tuning the SIEM and configuring sensors
- Less time spent on incidents than alarms
- More time for threat hunting
- Faster and more accurate scoping of malware outbreaks
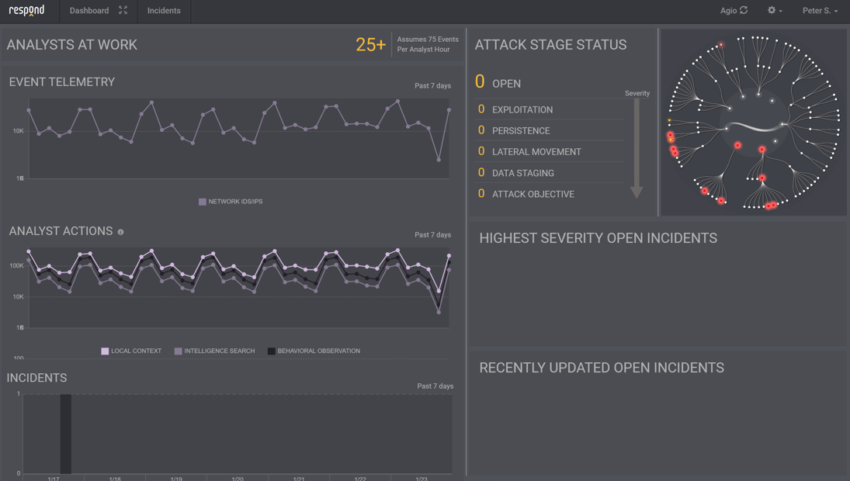
In an MSSP, the standard metric for Tier 1 SOC analysts is 75 events per hour at the console. Assuming the analyst sits at the SIEM console for 5 hours of concentrated work, the maximum number of events they observe is about 375 per day. Of course, being human, they are capable of thinking about only seven events at a time. Respond Analyst is comparable to almost hundreds of human analysts in terms of its ability to understand the amount of log event volume produced by most organizations. It does so consistently and without the need for complicated SIEM rules and inter-tier communications. Respond Analyst is not merely a replacement for Tier 1 labor. It does that, but it also adds capabilities that are far beyond the capabilities of any individual human analyst or team.
It’s why we adopted the technology into our service as soon as we did. If you know us, you’ve heard us say we’re tech-snobs. We’re constantly evaluating the market for best-in-breed tools, technology, and platforms to fuel our service to deliver a more secure, reliable, and resilient portfolio to our clients. For Agio, this is what it’s all about. Contact us if you’d like to have a deeper conversation about how our MDR capabilities might be able to support you.
SUBSCRIBE
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.

