Incomplete XDR Coverage Leaves You Vulnerable
Imagine yourself in this situation: You’re a diverse global company. COVID-19 is everywhere and hurting business, so you have to furlough some people. They’re still technically on the payroll and have company-issued equipment, but they’re supposed to be on leave and not using that equipment. Except one of those users connects to the company VPN, checks email, clicks on a phishing email link, and just like that, your entire network is infected with ransomware. You have no incident response plan in place to mitigate the impact. The result is your nightmare: operations are shut down, creating a significant impact on your business and productivity, not to mention your bottom line.
Could it have been avoided? There are four things at play here: phishing, the breadth of your extended detection and response (XDR) service, incident response, and endpoint detection and response (EDR).
Phishing
Phishing is a common problem, but companies become complacent. You know what you need to do, but you ignore it as a non-issue because your employees have done the phishing simulations, and everything was caught—this confirmation bias can put your data at risk.
The threat landscape is continuously changing, and you can’t account for user behavior. Users have to understand that the onus is on everyone and that even they could be an unwilling internal threat. (And to be clear, in most cases, an internal threat doesn’t mean the user is purposely sabotaging the system. It’s usually that a user made a mistake—like clicking on a bad link—that happened to have very big consequences).
Sticking with our scenario above, the user clicked on a phishing link that started a ransomware kill chain. Ransomware is malware sent out by a bad actor who is motivated by criminal intent.
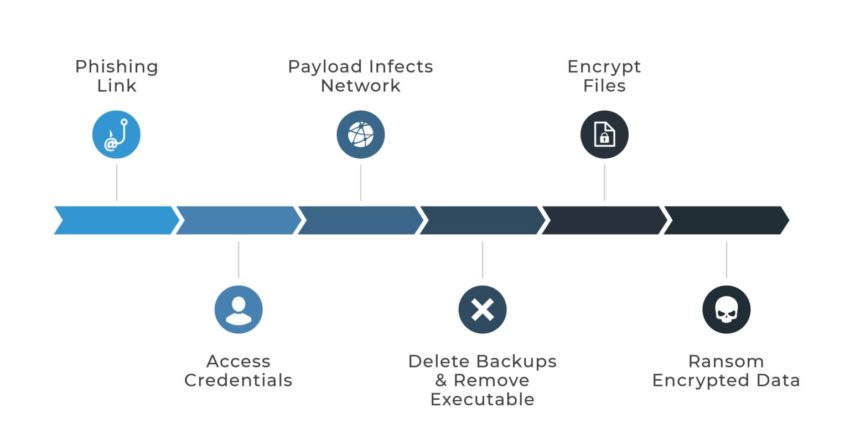
When the kill chain was activated, the compromised workstation performed a series of actions the user couldn’t see—which went exactly as the attacker planned. The malicious script used administration tools already present in the environment. This is known as living off the land, a technique that uses resources already present on a host or in a network for malicious purposes, and in this case specifically, for lateral movement throughout the network.
The malware proceeded to uninstall Windows Defender and access credentials via dumping tools.
Ransomware encrypts your files and holds them hostage, then the attacker asks for money to decrypt them. In many cases, the bad actor asks for money twice: once to decrypt the data and again to buy back the copies so they aren’t distributed to other venues like the public or dark web.
Here’s a sample of a ransomware note you may receive when your network is infected:
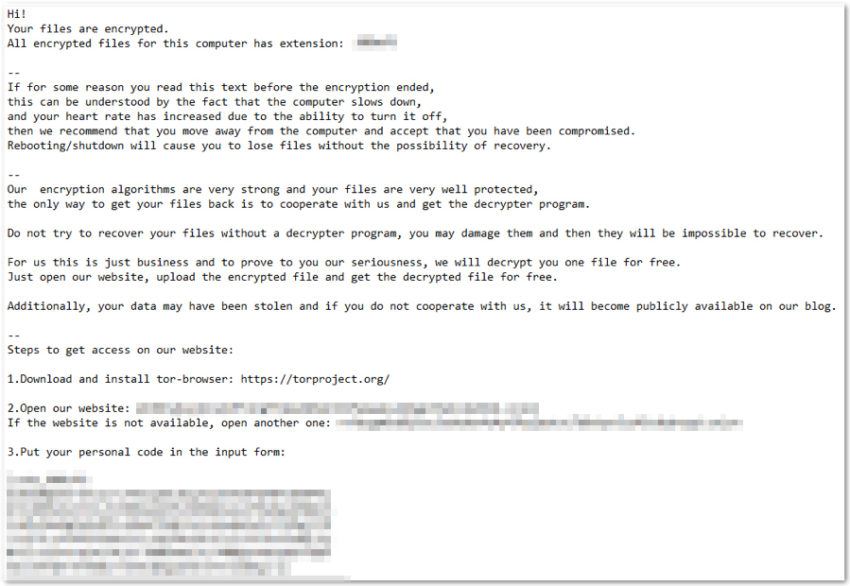
Ransomware can be wormable, meaning once it infects the initial computer, it propagates throughout the entire network, deleting backups and removing the executable before encrypting files.
The time it takes to mitigate and remediate the situation, especially if you don’t have the right tools, is valuable and affects both productivity and the bottom line. Those tools include an XDR service that has at least incident response and EDR.
Incident Response
Agio’s XDR service is a full-service cybersecurity solution that includes incident response, email threat protection monitoring, EDR (powered by Cylance), phishing protection, and more.
Let’s say our global company purchased a stripped-down version of Agio’s XDR services simply to tick the XDR box to show they had a 24-hour monitoring service. Now they have XDR, but they lack crucial components—including incident response.
With a stripped-down XDR solution, Agio wouldn’t have agents and sensors in every location related to the environment. There’s what Agio can see, and what the company can see—and the company isn’t cataloging which machines have been impacted. Unfortunately, incident response is a solution they really needed when the ransomware spread through the network. They hadn’t planned for the unexpected—they’d never implemented an incident response plan before and had no procedures in place.
As an XDR and incident response partner, Agio suggests specific solutions to avoid as much damage as possible while getting you up and running with as little interruption as possible (this isn’t an exhaustive list):
- Isolate your backups and reset service accounts and passwords so the backups can’t be attacked.
- Make sure your server message block (SMB) is up-to-date and not vulnerable.
- Change passwords everywhere—your accounts and your users’ accounts.
When Agio does a root cause analysis, we often find the bad guys get as far as they do because a company isn’t adhering to brilliance in the basics. For example, one of the topmost reasons bad actors are able to breach a company’s system is that the company used the default administrator account in Active Directory. Changing that password is a basic deterrent. Without that change, a bad actor still has a way in and can take over that account. Then they have rights to the entire domain and can do whatever they want. They can take Active Directory, steal it, export it, they could take it down. They could strip out the other domain admins. They can cripple the network.
As an aside, using the built-in admin accounts also makes it hard to do tracking successfully. We can’t overstate this one: please don’t use the default admin accounts.
Traditionally, incident response gets split up: managers go to this side; technical resources go to that side. Then Agio does a short cadence report update with both sides—this is where things can go sideways. When technical issues are brought up (e.g., changing passwords across the board), business usually trumps security, and passwords may not be changed, or another technical issue may not be implemented. Why? Because management wants to get production up and running to avoid losing money. Understandable, to be sure.
The problem with that thinking is that the bad actor has all the unchanged passwords. If you don’t change them, you’re opening yourself up to reinfection. Even when Agio restores the network and eradicates the malware, the unchanged passwords are a weak spot—an invitation, if you will—that allows the bad actor to come back in and restart the process. We explain this and warn clients of the consequences, but many times business wins over security, and that’s where it ends.

Endpoint Detection & Response
Let’s continue to play out our scenario. While the company doesn’t have an incident response plan in place, they do have their own EDR. Unfortunately, it’s subpar (something Agio would catch and warn against). Additionally, the EDR wasn’t put on every endpoint, and that’s a problem. When you partner with Agio for XDR solutions, include our tested and trusted EDR, and put it everywhere to protect yourself.
With the endpoints are unprotected, the propagating ransomware uses PSExec to move through the network quickly. Agio would have starts and stops of the service, but there wouldn’t be an alarm in place for PSExec laterally moving across the network.
And while the company has our basic XDR, the data feeds were their own tools, so Agio had no other capability other than notification of alarms and suspicious traffic via the SOC. Without Agio’s full range of services, we wouldn’t be able to catch the malware before they did. However, Agio takes care of our clients. Once our XDR engineers know about the breach, they can remediate and diagnose the issue the company is facing.
To start, Agio’s engineers would immediately deploy a trial copy of our standard EDR platform (powered by Cylance), spin up a tenant, and have it working throughout the entire environment. Cylance can detect whether one of the admin accounts is compromised, and our engineers can halt all forward movement of the ransomware.
Summary
If there’s one thing you should do for yourself, it’s making sure you have a complete XDR service that works and is being monitored by a partner like Agio. Our complete XDR services offer unified security management, incident response, EDR, email threat detection, and phishing protection.
When you have an incident, you’ll be glad you have a partner who has seen these problems before and has the talent to respond immediately. This is where Agio’s XDR team shines. We’ll be there for you—whether you’re a global company or not—around the clock. We can alert you to possible threats, and help you bring your systems back online regardless of how spread out your teams are.
Give us a call to set up your complete XDR solution. We’re here to help.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.





