How to be a Healthcare BA and Not Lose 25 Million PHI Records
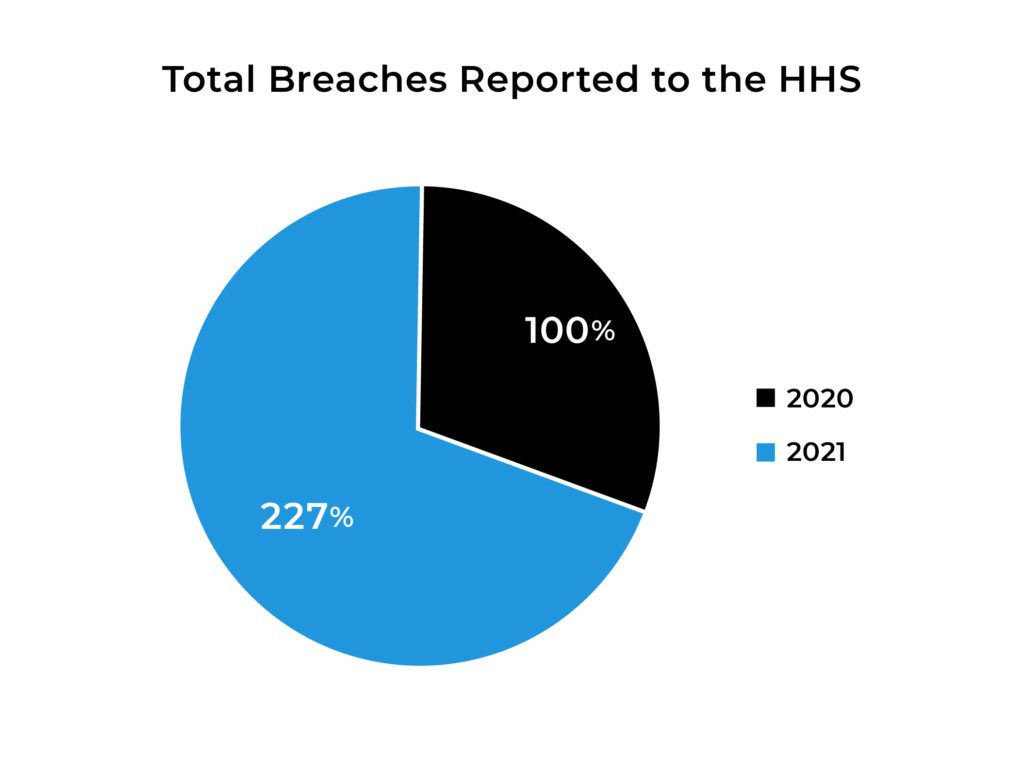
Cybersecurity in healthcare had a big year, with breaches increasing by 127%. On the upside, the American Medical Collection Association (AMCA) found its way out of bankruptcy when 41 Attorneys General agreed on how to handle the 2019 breach affecting 25 million PHI records. This does not give us warm fuzzies, but does point out the importance of adhering to Agio’s “Brilliance in the Basics” in the evolution of your organizations cybersecurity risk.
By now you may have already heard that hackers stole the 25 million PHI records entrusted to AMCA from LabCorp, Quest Diagnostics, and BioReference Labs.
On March 11 this year, Attorney General Josh Shapiro announced: “Pennsylvania, along with 41 Attorneys General, has settled with Retrieval-Masters Creditors Bureau, doing business as the American Medical Collection Agency (AMCA), resolving a multistate investigation into the 2019 data breach that exposed the personal information of over twenty-five million individuals. AMCA served as the debt collector for LabCorp, Quest Diagnostics, BioReference Labs and other medical service providers.” [PR1]
OCR rules requires business associates to report breaches within 60 days. This business associate announced their breach in May 2019, 8 months (240 days) after the incident. Contents included the name, date of birth, address, phone number, provider name, balance information, payment card information, bank account information, social security number, and information about lab results.
To release AMCA from bankruptcy, the Attorneys General forced the agency to do what it should have done prior to the breach:
- implement a healthcare security program,
- hire a qualified CISO (Chief Information Security Officer),
- engage a qualified third party to complete risk assessments annually, and
- cooperate with the state which includes:
- reporting results within 15 days,
- responding to all requests for information from the AG,
- granting access to servers,
- providing truthful testimonials,
- complying with requests for their employees, representatives, and agents to provide testimonies which includes their address, cell phone number, and email address.
AMCA never created its own records. It received the records from the labs so it could bill and collect payments for them. However, not creating the data does not excuse a business associate from its responsibility to protect it. The OCR requires business associates to protect the data, regardless of who created it.
Why go after medical data from business associates?
Smaller business associates are easier targets, Still, they must compile with the rules of cybersecurity, even when they do not have the budget to manage an in-house team large enough to protect patient records.
Lack of access to security resources and the supporting security infrastructure makes them attractive to hackers.
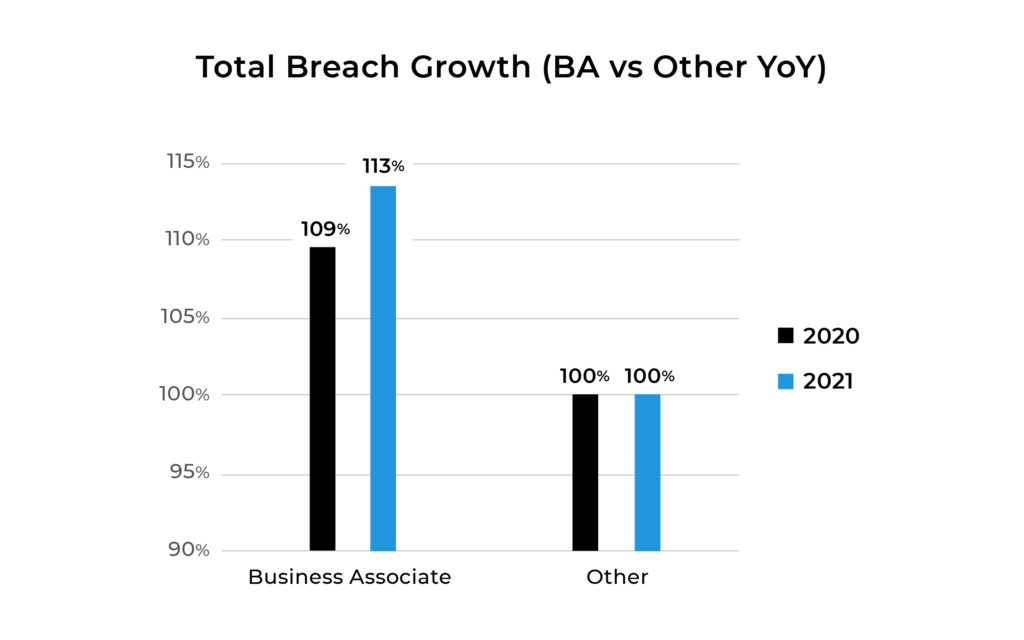
According to the US Department of Health and Human Services, (OCR) 13% more breaches occur against business associates than other healthcare organizations and the number is growing faster. (Q4 2021 is in progress). That makes them targets for both bad actors on one side and legislators protecting patients on the other. Typically, business associates put their energy into their products rather than security. But the landscape has shifted. These healthcare organizations must adapt to the rules. Attorneys general will protect patients’ rights first.
The genuine gold is in the PHI data. It is valued 50X more than the rest.
Because PHI data combines governmental, medical, and financial information, it is the richest, most dense data available on a large scale.
We create our data when we visit the doctor, specialist, pharmacist, or pay bills for medications, use services based on lab results, or choose treatment options. In addition to this data, there is also an entire wealth of more valuable information – clinical research data.
Clinical research is the billionaire of PHI data, especially for cyber-terrorists. Covid-19 has dramatically increased research data; the source for intellectual property, patents, and approvals. Cyber terrorists can use it to sabotage the development of new drugs and misguide emergency solutions intended to save us. Even more, bad actors can use this data to erode trust in our own institutions by creating disinformation that appears credible on the surface. That is why both criminals and cyber-terrorists love it.
Bad actors do not steal PHI data just to skim a bit of money by submitting bogus transactions. Bogus transactions only test data quality. A transaction may not even use a payment method. In a portal, a bad actor may test for other details that are valuable to buyers. Data on the blood type, other medications related to the patient, data used to determine the bill and how to collect it. Each successful access point raises the value of the data – a successful transaction. The data itself holds the payoff.
According to Experian, healthcare data is worth $1000 per record on the black market, compared to $5.40 for the next highest value record (a payment card).
That makes the AMCA hack worth twenty-five billion dollars (about $77 per person in the US) in the cyber-terrorism marketplace. That is not bad for a hacker who figured out how to access the payment portal – his method of ingress.
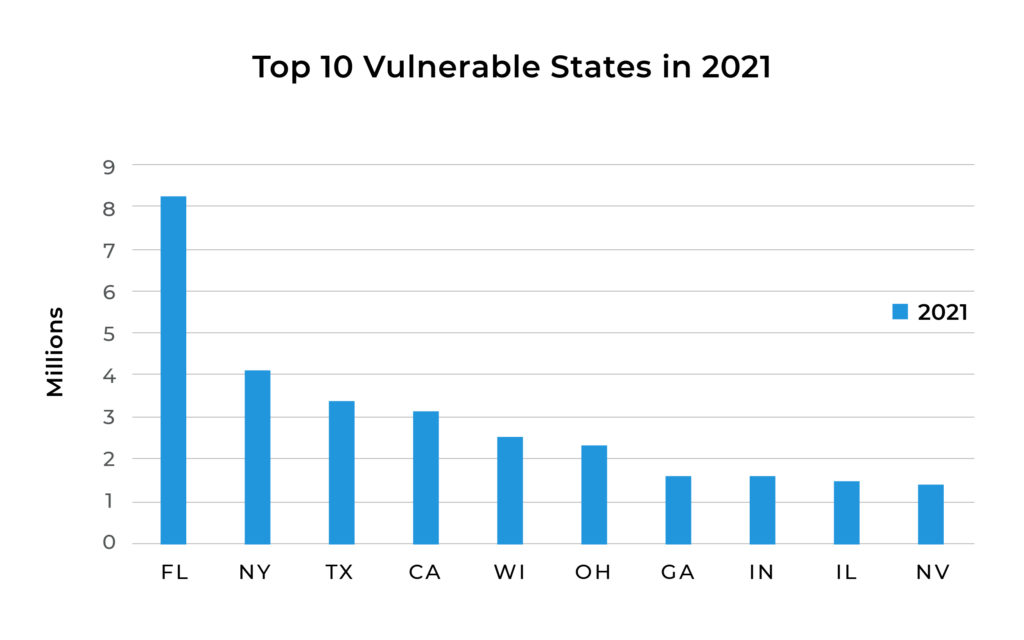
The Top 10 states with high attack rates
Hackers can use the odds to work faster if they choose primary targets. HHS tells us Florida, New York, Texas, California, and Wisconsin are the top five out of ten most attacked markets.
You are wondering “If all the big players are protected, aren’t we safe?”
AMCA is only one business associate out of a minimum of 33,500 others. Business associates come in a variety of forms and sizes. Each one either creates or accesses PHI data.
Beyond the over 9,000 urgent care centers in the US, there are over 17,000 locations for primary care. Covid rapidly grew the market for Internet health services like eHealth. The definition is broad, but the responsibility to protect patient health information is not.
HHS define business associates under 45 CFR 160.103: as follows:
Except as provided in paragraph (2) of this definition, business associate means, with respect to a covered entity, a person who: (i) On behalf of such covered entity or of an organized health care arrangement (as defined in § 164.501 of this subchapter) in which the covered entity participates, but other than in the capacity of a member of the workforce of such covered entity or arrangement, performs, or assists in the performance of: (A) A function or activity involving the use or disclosure of individually identifiable health information, including claims processing or administration, data analysis, processing or administration, utilization review, quality assurance, billing, benefit management, practice management, and repricing; or (B) Any other function or activity regulated by this subchapter; or (ii) Provides, other than in the capacity of a member of the workforce of such covered entity, legal, actuarial, accounting, consulting, data aggregation (as defined in § 164.501 of this subchapter), management, administrative, accreditation, or financial services to or for such covered entity, or to or for an organized health care arrangement in which the covered entity participates, where the provision of the service involves the disclosure of individually identifiable health information from such covered entity or arrangement, or from another business associate of such covered entity or arrangement, to the person (2) A covered entity participating in an organized health care arrangement that performs a function or activity as described by paragraph (1) (i)of this definition for or on behalf of such organized health care arrangement, or that provides a service as described in paragraph (1) (ii) of this definition to or for such organized health care arrangement, does not, simply through the performance of such function or activity or the provision of such service, become a business associate of other covered entities participating in such organized health care arrangement. (3) A covered entity may be a business associate of another covered entity.
As service providers in the healthcare industry, every organization is responsible for protecting patient data and its integrity in the custody chain. However, smaller business associates do not have the budget needed to protect their sensitive records.
To see a clearer picture, we can look at the National Association of Free Clinics. There are over 1,400 free clinics alone serving people who fall through the gaps. Each of them survives on shoestring budgets. They have patient data but do not have the budget needed to protect the records and their funding is scarce. These clinics and pharmacies receive little to no state or federal funding, they do not receive HRSA 330 funds, and they are not Federally Qualified Health Centers or Rural Health Centers. Healthcare cybersecurity programs do not have the same priority as the medical specialists who need to serve their communities.
“My organization is much smaller. Is this really necessary?”
This is a numbers game. Hackers can hit large numbers of smaller companies for higher averages in payout Many business associates are smaller, but they still access the richest data in the world. Every player matters in the health care infrastructure game.
Hackers see business associates as opportunities. Business associates stay focused on immediate health needs. They cannot create a security team, nor do they have a CISO to evolve governance over a continually evolving security policy and strategy.
Enforcement of a contract’s terms is critical to cybersecurity and compliance requires engaged monitoring and initiative-taking testing. Failure to act quickly, as in AMCA’s 8-month delay, is dangerous to both the company’s reputation, financial health, and to the patient whose record was snatched.
What you can do today.
If you are a business associate, you are at risk, but are you at the level of doom and gloom? Not if you prepare. There are six fundamental ways to minimize your chances of an attack.
- Implement multifactor authentication across the network.
- Deploy consistent security configurations.
- Restrict privilege to what an employee needs to do the job.
- Continually train everyone in cybersecurity hygiene.
- Keep systems and software patches up to date.
- Practice your team’s incident response plan annually, as if it is a real-world emergency.
Like the American monk, Thomas Merton, taught his disciples: “You can move a mountain with a teaspoon if you show up with your attention for a brief time every day.” Be smart, start small, pick the easy opportunities, and do a little more again tomorrow. We have packaged the 6 steps above into an easy to implement playbook to help your organization.
Share post
Featured Posts
Connect with us.
Need a solution? Want to partner with us? Please complete the fields below to connect with a member of our team.




